Information security management

1
The risks of information security

2
Cyber Security Framework

3
Source of business marketing

4
Proced-manager in design

5
Information security specialist

6
Information Security Management System

7
Information security curator

8
Compliance tools

9
Security Management System

10
Computer innovation

11
Information technology in business
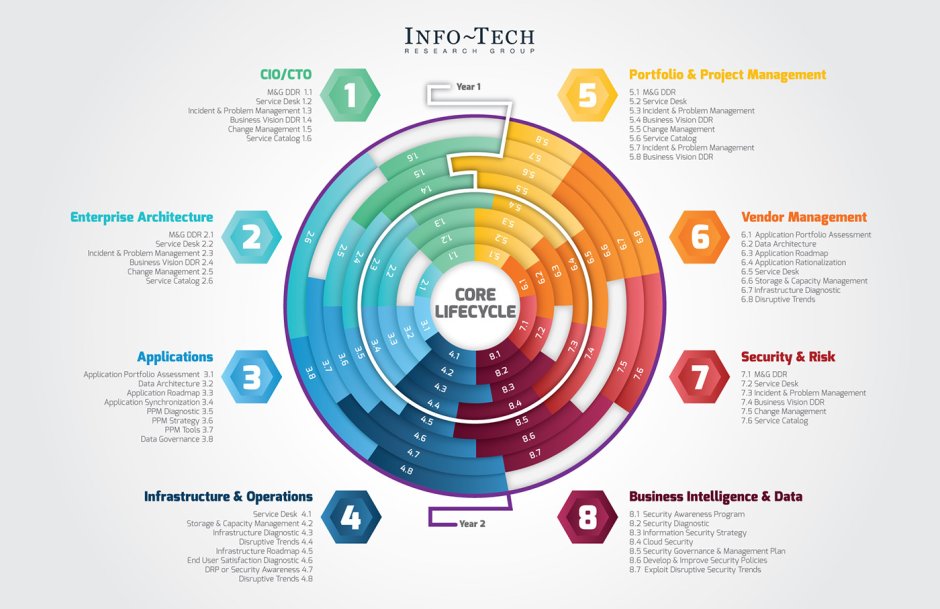
12
Roadmap web designer

13
Information Security

14
CyberSecurity Maturity Model

15
SIEM system

16
"Information Management" infograph

17
IT consulting

18
Information Security

19
Business Assessment Business

20
Information Security Management System

21
Information security CISO

22
Cloud system in logistics

23
ITIL process model

24
Security Information Management

25
Cyber Security Sim

26
Managed Security Service Provider

27
Lifecycle Security diagram

28
Data Subject pictures

29
Information Security

30
Cyber CAMP Information Security

31
Cyber Security

32
GRC system

33
Information security

34
Digital technologies

35
Vulnerability of the security system

36
Information technologies Word

37
GRC ED-1

38
It department Structure

39
ITIL V3 structure

40
Outsourcing IT infrastructure of customers

41
Cyber backup cyberspace

42
Data Management Strategy

43
Portfolio strategy

44
Information Security Flat

45
Computer techologies

46
Presentation of Communications Technologies

47
Abilities KnowLEDGE SKILLS

48
Security Operation Center SOC

49
Information Protection Vector

50
Information Technology

51
Cyber Security Framework

52
Schedule Security System

53
Cyber Security Roadmap

54
Information Security Management or ISM

55
SIEM Habr system

56
The Hierarchy Product Manager

57
Information security specialist illustration

58
Information technology in the economy

59
Data Governance

60
Information Security

61
Cyberspace diagram

62
Communication technologies of the Internet of things
See more photo ideas
Comments (0)

